
IBM Security Explores How to Secure Your Journey to Hybrid Multi-Cloud
From mis-aligned business strategies to shared security responsibility models in the cloud, to the growing tools and technologies available, security in the cloud can seem daunting, especially when just adopting traditional security controls in the cloud may not always be the best approach.
However, the future of modern business depends on having secure hybrid cloud and multi-cloud solutions in place, according to Amanda Sherman, product manager of Cloud Security Services at IBM Security.
Speaking during the Security & WFH break-out presentation “Securing your Journey to Hybrid Multicloud” May 12 at the annual Hollywood Innovation and Transformation Summit (HITS) Spring event, she said: “When it comes to the move to cloud in general – a shift toward digital transformation – there is really one word that likely resonates with anyone who is embarked on that journey, and that word is change.
That is the case whether it be changes to the way your organisation is deploying applications to changes in the way data is “mass proliferating across everywhere to the fact that your infrastructure is changing and it’s cascading across multiple environments now,” she noted. “Things are changing and the success of this entire digital transformation journey is hinging on the modernisation and adaption of your security programme for this new hybrid cloud reality.”
 We are “finally getting to a point now where organisations aren’t sidestepping the security question anymore,” she said, explaining: “The trend is shifting. Security is moving away from being treated as a checkbox. But just because you’re prioritising security now doesn’t mean it makes things any easier. In fact, while the business is going through this digital transformation, the security team had been historically left out of the equation, which results in a lift-and-shift approach of legacy security controls to protect these new cloud workloads. But that doesn’t translate well for multiple reasons.”
We are “finally getting to a point now where organisations aren’t sidestepping the security question anymore,” she said, explaining: “The trend is shifting. Security is moving away from being treated as a checkbox. But just because you’re prioritising security now doesn’t mean it makes things any easier. In fact, while the business is going through this digital transformation, the security team had been historically left out of the equation, which results in a lift-and-shift approach of legacy security controls to protect these new cloud workloads. But that doesn’t translate well for multiple reasons.”
For one thing, on-premise, an organisation has “complete control and visibility,” with a corporate network that it trusted, she noted, adding: “The movement of data and critical assets was well-contained for the most part, whereas, in cloud, all of that changes. Your perimeters dissolve. You now have dynamic asset points and user groups. Your management ports are exposed to the Internet, which in turn unfortunately exposes maybe some lax application security practices, some haphazard protection controls or lack thereof and, finally, your pairing of dynamically flowing data and dynamically deployed workloads with static and incomplete controls that really aren’t giving you the level of protection or visibility that you need.”
How successful an organisation’s cloud journey will be “depends on not just the business transforming but the security programme transforming as well because that legacy security programme and controls … don’t translate well to cloud as is and security teams are now faced with a lot of new security challenges,” she pointed out.
Common Challenges
One of the most common challenges that IBM Security sees across organisations is that the security and digital transformation strategies for the business are not aligned, she said.
“We’ve had countless conversations with organisations that are rapidly building up and executing on their digital transformation strategy,” she explained. “Then they have their siloed security strategy that they’re trying to maintain and keep up with. But these two things [are] not moving in the same direction or at the same pace. Security doesn’t have a voice at the table and so we see that cloud transformation happen often times ahead of their readiness to really secure that journey.”
There are, meanwhile, “tons of new tools and tech entering the security vendor ecosystem, especially when you think of all the native security capabilities being built into cloud platforms,” she noted. “But just because those native controls are provided by the cloud provider doesn’t mean they’re managed by them. You now have to navigate the waters of shared security responsibility with your cloud provider and ensure you have the right skillsets to even manage these new controls and technologies.”
Another challenge is that traditional security rules in the organisation are losing control and visibility, she pointed out. In the cloud, “it is so much easier for lines of business to deploy new workloads without security review or even awareness that they’re happening or use Software-as-a-Service (SaaS) services without proper sign-off in lower security maturity organisations and so this kind of transforms where and how you implement security because you know how new folks like DevOps and infrastructure architects who are more in that front seat for ensuring these deployments are secure,” she said. The problem is “those folks aren’t security experts,” she noted.
Organisations are simultaneously “dealing with competitors innovating more rapidly so the struggle here is finding that frictionless means to implement security without impacting that development velocity which in turn is a huge challenge,” she said.
“The threat landscape is expanding, which is shifting your need to adapt from relying on traditional network security as your safeguard to a more comprehensive, multilayer security approach,” she explained. “What this has also done is siloed your visibility into threats and compliance, which is a huge challenge. And we see organisations a lot of times trying to solve this first by enabling a bunch of log flows in the cloud environments. The public clouds provide so many options in terms of enabling logs and getting access to data and telemetry and insights. But, without the right processes and governance models in place to really dissect and decipher from that data what’s important and how to prioritise it all, how to centrally correlate it and make decisions from all of that data, all you end up with is data and alert fatigue, especially when we’re just enabling logs because we can.”
Another “huge challenge we see organisations struggling to manage,” meanwhile, are cloud misconfigurations, she said. In the cloud, she noted, attackers work on “complex, sophisticated attacks.” However, “they’re also focused on low-hanging fruit opportunity, which are cloud misconfigurations,” she pointed out.
“Last, certainly not least” among challenges that organisations commonly face is the “skills gap,” she told viewers, noting they are “struggling to find and retain that right mix of experience and knowledge across both cloud and security.” It has become like a “hunt for the purple unicorn” and when you finally find it, an organisation “can’t retain it,” she noted.
Security, meanwhile, can’t be approached differently across an organisation’s premise and cloud environments, she said, explaining: “What’s needed is a re-vamped security programme that provides consistent security controls and architecture across your workloads, regardless of where they reside, and then centralised visibility into threats and compliance.”
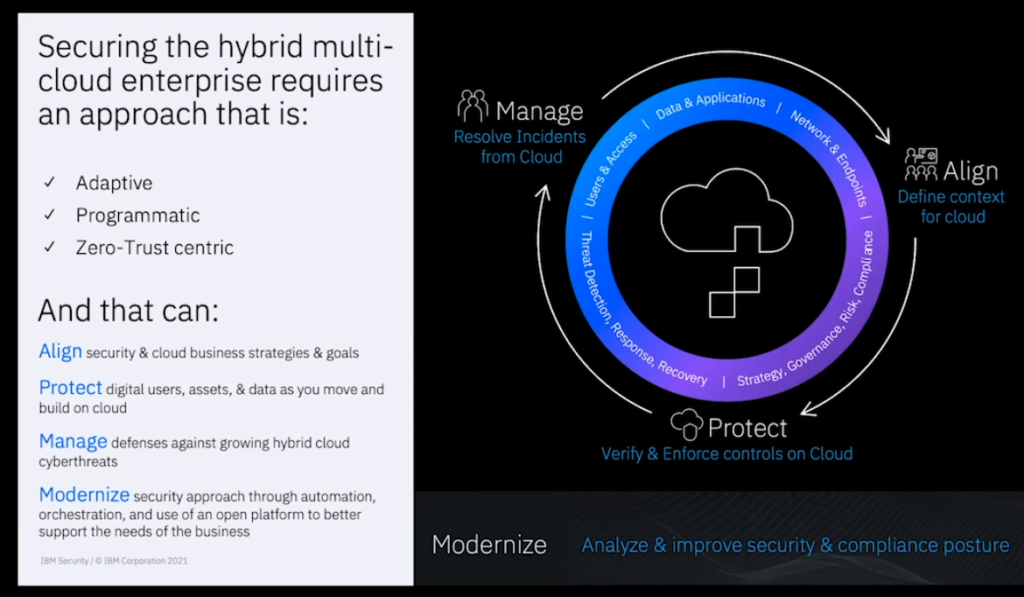 The Necessary Approach
The Necessary Approach
Securing the hybrid multi-cloud enterprise requires an approach that is: adaptive, programmatic and “zero-trust centric,” according to IBM Security.
Organisations “need an overarching strategy and governance programme that’s modernised for cloud [and] you have to have a consistent approach to protect workloads across that entire environment,” Sherman explained. “On the cloud side, you need to be diligent on detecting and responding to cloud mis-configurations. From a network and access perspective, you really have to re-think things from a more multi-layer, kind of zero-trust centric approach.”
And it is important to realise that “not everything will happen at once,” she said with a laugh, noting: “Moving to cloud is a journey for both you and your organisation, as well as your security programme.”
The first step in the cloud journey for many organisations is an “ad-hoc” approach in reaction to an event that happens and playing catch-up with legacy security controls after the business has started migrating to the cloud, she noted.
Then an organisation should start adapting its security program for cloud by “rationalising” on the right set of controls and gaining centralised visibility to threats and compliance, according to IBM Security.
“Once you’ve covered the basics, then you can start refining that programme” and this is where some of the zero-trust principles come into play, Sherman said.
The fourth step on the journey is a “fully optimised for cloud security programme” that is automated throughout and uses artificial intelligence and machine learning to take faster actions against threats, she said.
To align a security programme, the “must-have top 3” components are: having a defined cloud security strategy; discovery and classification of critical data and who has access to it; and a centralised threat management and compliance strategy, according to IBM Security.
The “should-have” components after those are: macro-level architecture across security domains; secure development practices implemented; an optimal offensive testing strategy defined; and “deep resiliency” plans that are in place with cloud vendors and a third-party risk management strategy established, according to the company.
Look at not only where your organisation is now but where it is going down the road while building out a security strategy, Sherman suggested to viewers.
Concluding, she said that, with so much to consider, it is essential to make sure that an organisation has covered all the basics: assessing its current environment and strategy; understanding what and where its critical data is; and reviewing its current cloud compliance posture.
To view the entire presentation, click here.
HITS Spring was presented by IBM Security with sponsorship by Genpact, Irdeto, Tata Consultancy Services, Convergent Risks, Equinix, MicroStrategy, Microsoft Azure, Richey May Technology Solutions, Tamr, Whip Media, Eluvio, 5th Kind, LucidLink, Salesforce, Signiant, Zendesk, EIDR, PacketFabric and the Trusted Partner Network.
